Background
If you’ve ever undertaken a security risk assessment (SRA) yourself, or engaged a security risk consultancy to do one, you may have wondered whether it was as comprehensive as it could have been, and if could it withstand serious scrutiny. The real test, as some practitioners will attest to, is whether it could stand up to serious legal scrutiny, and whether assertions are based on a well-argued basis, or whether they’re simply the opinion of the assessor.
Part of the notion of completing a defensible assessment is to first understand where the rest of the industry is at, so that a measure of the relative credibility of a proposed approach can be obtained. Good practitioners will do this and use the information to regularly improve their approaches to, and quality of their deliverables.
The Challenges
One of the key challenges in knowing how a SRA compares is to be aware of where better practices can be found, and to find the time to review them regularly. There are many industry organisations dedicated to security matters, and risk assessment/management practices lie at the heart of many of them. Across the traditional security and cyber-spectrum, some that are widely recognised include:
- Institute for Strategic Risk Management (ISRM).
- Security Executive Council (SEC).
- Information Systems Audit and Control Association (ISACA).
- ASIS International (ASIS).
- You may even look to a proactive security risk consultancy to see what they’r eoffering – many offer free content through their websites.
Like any trade, a detailed understanding of its body of knowledge affords the highest likelihood of a genuinely professional outcome. In this regard there are numerous other entities, including standards bodies themselves, and abundant white papers and reputable blogs where better practices and good advice can often be found.
Further, and while there are some staple and straightforward components of SRAs, a significant degree of expertise really is usually required to put them together in a logical and meaningful fashion. Indeed, the absence of methodological rigour is a frequent casualty.
________________________________________________________________
RELATED ARTICLES: Musings On Security Risk Assessments | The Benefits Of SECTARA’s Advanced & Intuitive Risk Assessment Methodologies | What Is A Risk Assessment Template? | What Is A Risk Assessment Matrix?
________________________________________________________________
Should you Engage a Security Risk Consultancy?
It’s not always necessary to engage external support – if internal resources are available and are up to the task then they should be used. If they need to be developed, take the time to pick decent courses – there are many that simply run by the numbers and teach too much in the way of non-practical methods.
If a security risk consultancy is to be engaged, make sure to ask for an example of the product you’ll be receiving. That will set mutual expectations, and because you’ll invariably be supplied a good looking product, the consultant will feel compelled to match its quality.
What’s in a Good SRA?
Whether it be cyber or protective security focused, a good SRA will be one that:
- Articulates which methodology is being applied, how it works and why it is credible in the context of the assessment.
- Tells a logical ‘story’ by providing background and sufficient context to the process being undertaken, and the drivers for it.
- Articulates the compelling reasons as to why change is needed (much like a business case).
- Clearly defines the assets (physical, personnel, information etc.) that require protection, and highlights the relative importance of those assets (i.e. through a criticality analysis).
- Provides sufficient background to the various threat actors and acts that may impact those assets by way of a threat assessment.
- Identifies the risk controls that are used to protect against those threats, and how effective each of them is at doing so (i.e. a Risk Control Effectiveness assessment).
- Describes areas of vulnerability and risk within the organisation, consistent with the scope of the assessment.
- Clearly articulates current risks and assigns them ratings consistent with organisational risk criteria (i.e. not criteria supplied by a third party, unless the organisation prefers an independent approach).
- Evaluates current risk ratings to identify which exceed tolerable thresholds.
- Identifies pragmatic and cost-beneficial risk controls that reduce the likelihood of a threat act being successful (resulting in associated risks being realised), and/or the consequence of an incident (through effective preventative, response and recovery controls).
- Supports its recommendations through defining the benefits to the organisation, in support of its strategic and operational objectives.
- Considers the SRA process a critically discrete and keystone element of developing a security/risk treatment plan.
- Is monitored, reviewed and evolved/improved over time (rather than recreated periodically).
Security risk methodology
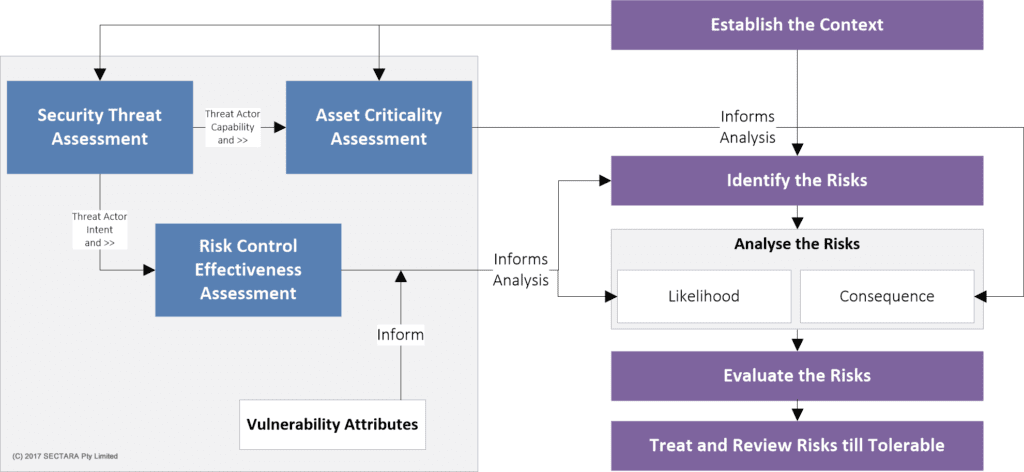
Condensed Security Risk (Assessment and) Management Process
The diagram above shows a slightly modified version of what, at the time of writing, the Australian Government requires its Agencies and Departments to implement when conducting a SRA. It was around well before Government imported it into the Protective Security Policy Framework (PSPF), however.
The key requirements of this methodology, and by extension a good assessment, is effectively canvassing the sub-assessment stages on the left had side, while simultaneously adhering to ISO 31000 – Risk management on the right. This approach contains elements that are incorporated within most globally accepted security risk methodologies.
The Takeouts
The production and distribution of underwhelming assessments does the organisations affected, and indeed the industry, a disservice, as stakeholders deal with periodically unsubstantiated findings and recommendations.
Every SRA represents a challenge for the assessor, and the scope and context of most requires nuance and expertise in the security risk ‘trade’ to deliver good product.
It is imperative, therefore, that those who wish for continuing credibility growth in the sector, and indeed stakeholders themselves, become more discerning in selecting suppliers, and active in demanding high standards.
All assessments should demonstrate logically arranged arguments canvassing the elements listed within this article. If not, stakeholders should feel comfortable asking why not.
Yours in SRM,
Konrad Buczynski
Konrad was a graduate of the Royal Military College Duntroon and served as an Australian Army Officer and telecommunications specialist until 2001. He has helds roles as Director of the Australian Centre for Security Management and Chief Security Officer | Crisis/Business Continuity Program Manager at Thales Australia-New Zealand, the region’s largest Defence Prime Contractor at the time.
A Certified Practising Risk Manager, Registered Security Professional, member of numerous security working groups and technical committees and designer and author of innumerable security risk management programs, Konrad was the architect and co-founder architect of SECTARA. He is a company Principal and SECTARA’s Managing Director.
Did you known that the Security Risk Management Aide Memoire (SRMAM) is free to all SECTARA subscribers (yes, even on the free plan).
How to get started with SECTARA
If you see the same great benefits that we do in SECTARA, there are several methods to get started:
- Register for one of our Bronze, Silver or Gold Plans.
- Sign up to our absolutely Free Plan.
- Arrange an online demo.
- Contact us
As a valued subscriber, you will be comprehensively supported via our Ticketing System and Knowledge Base, and you can still always contact us direct when you need to.






