What Is a Risk Assessment Matrix?
A risk assessment matrix is the table (matrix) used for allocating risk ratings for risks that you identify, based on two intersecting factors: the likelihood (or probability) of a security risk-based event occurring, and the consequence (or impact) to an asset if it did. Such a matrix is vital to any risk assessment template as it is used to derive both current and treated/mitigated risk ratings.
Why Use a Risk Assessment Matrix?
As discussed in a previous post, the following data is expected to be documented within the risk assessment template:
- context (external, internal and security risk);
- assets and their criticality;
- threats;
- an account of the effectiveness of risk controls that currently protect assets from threats;
- an assessment of individual risks (using the risk assessment matrix), which derives current risk ratings;
- evaluation of whether these risk ratings are tolerable by the entity;
- recommendation of mitigation measures if they are not;
- re-assessment of individual risks (using the risk assessment matrix), which derives residual risk ratings; and
- the risk owner, and timings for implementation of the controls.
The risk assessment matrix is thus a critical component of the risk assessment, because without it identified risks cannot be assessed or evaluated.
The matrix below shows two axes: the vertical axis represents the Likelihood, and the lateral axis shows the Consequence.
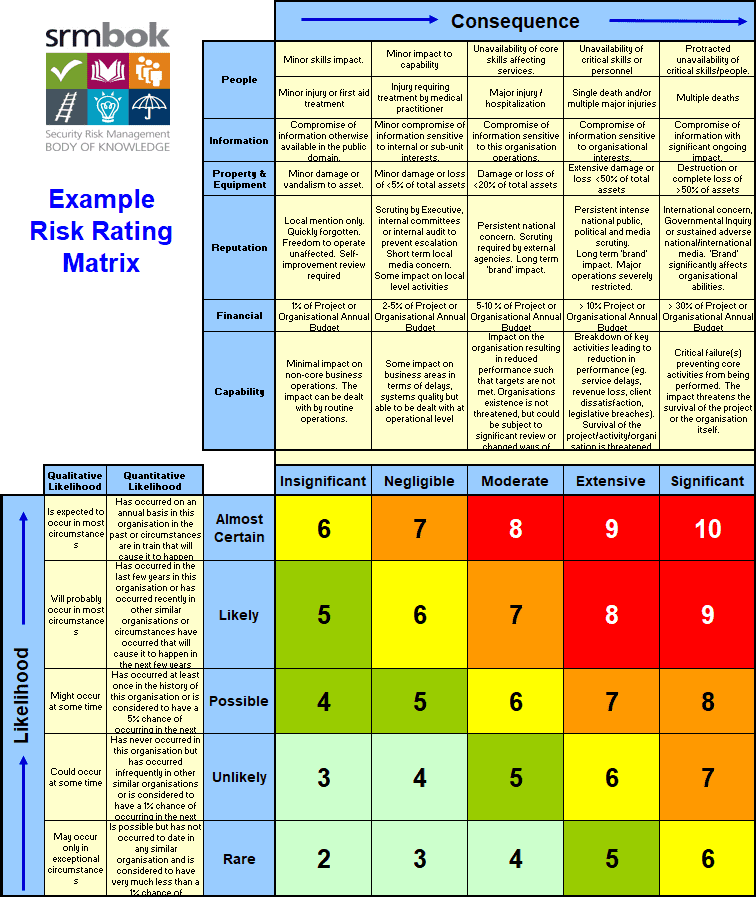
Image: Risk Assessment Matrix (Courtesy of Julian Talbot @ www.srmam.com)
Likelihood
While this matrix, which was originally included within the Security Risk Management Body of Knowledge (SRMBoK), presents measures of likelihood in qualitative and quantitative terms, it is not always necessary to do so. In truth, quantitative measures here can more realistically be referred to as semi-quantitative in any case (i.e. without a legend/reference the numbers are meanignless other than for comparative purposes).
It is most common within the security industry, where incident reporting figures are not always available, to apply a qualitative descriptor and approach within the risk assessment matrix; it is not necessary to include both qualitative and quantitative, as has been done here.
Labels used here, which include Rare, Unlikely, Possible, Likely and Almost Certain are qualitative. These are very commonly used by practitioners and thus represent a mainstream approach. So too the use of descriptors rather than numbers (e.g. Extreme/Catastrophic for red cells, High for orange etc.)
________________________________________________________________
RELATED ARTICLES: Musings On Security Risk Assessments | The Benefits Of SECTARA’s Advanced & Intuitive Risk Assessment Methodologies | What Is A Risk Assessment Template? | What’s in a Good Security Risk Assessment? |
________________________________________________________________
Consequence
Consequence criteria included within an assessment is not always as detailed as it is presented within the matrix above, but considering the impact of a risk across multiple areas of the business is a better practice approach. In this manner security acts as catalyst for other functional area managers to consider the potential impacts on their assets, and alert them to the need for action.
Again, the labels used here, which include Insignificant, Negligible, Moderate, Extensive and Significant, are common, but a range of others are also commonly used by assessors.
Using the Matrix
In utilising a risk assessment matrix, assessors decide, in their expert view, the likelihood that a defined risk will occur, then cross reference this (in this matrix) with the worst-case consequence that may result. Where these values intersect on the coloured/numbered area of the matrix, is the assessed risk level.
It would strike some then that the values/colours on this area of the matrix are key. When designing risk assessment matrices, assessors must ensure that this aspect of the matrix is very carefully considered.
Many assessors complete this instinctively, which can devalue the rigour and regard for an assessment. That said, many risk assessment stakeholders are not necessarily attuned to this, meaning that inaccurate risk results may go unnoticed. This would have the effect of significantly devaluing assessment results.
There are more scientific methods to design the elements of a risk assessment matrix, and https://riskmatrix.co/ is one tool that we look to. If you don’t give this area of your assessments quality attention, consider this – you’ve conducted an assessment for your stakeholders and they ask …”how did you decide what colours and ratings to use for each cell?” What would you say?
Worse still, let’s say your assessment ends up in court supporting some action that’s been taken – now it’s starting to get serious. Take our advice and make sure you get the matrix design right. You can then re-use it (unless your stakeholders suggest that you use theirs).
We’ve included such a matrix as part of the sample asessment included within each SECTARA account.
Yours in SRM,
Konrad Buczynski
Konrad was a graduate of the Royal Military College Duntroon and served as an Australian Army Officer and telecommunications specialist until 2001. He has helds roles as Director of the Australian Centre for Security Management and Chief Security Officer | Crisis/Business Continuity Program Manager at Thales Australia-New Zealand, the region’s largest Defence Prime Contractor at the time.
A Certified Practising Risk Manager, Registered Security Professional, member of numerous security working groups and technical committees and designer and author of innumerable security risk management programs, Konrad was the architect and co-founder architect of SECTARA. He is a company Principal and SECTARA’s Managing Director.
Did you known that the Security Risk Management Aide Memoire (SRMAM) is free to all SECTARA subscribers (yes, even on the free plan).
How to get started with SECTARA
If you see the same great benefits that we do in SECTARA, there are several methods to get started:
- Sign up to our absolutely Free Plan.
- Register online for one of our Bronze, Silver or Gold Plans.
- Arrange an online demo.
- Contact us for Platinum Plan pricing.
As a valued subscriber, you will be comprehensively supported via our Ticketing System and Knowledge Base, and you can still always contact us direct when you need to.





