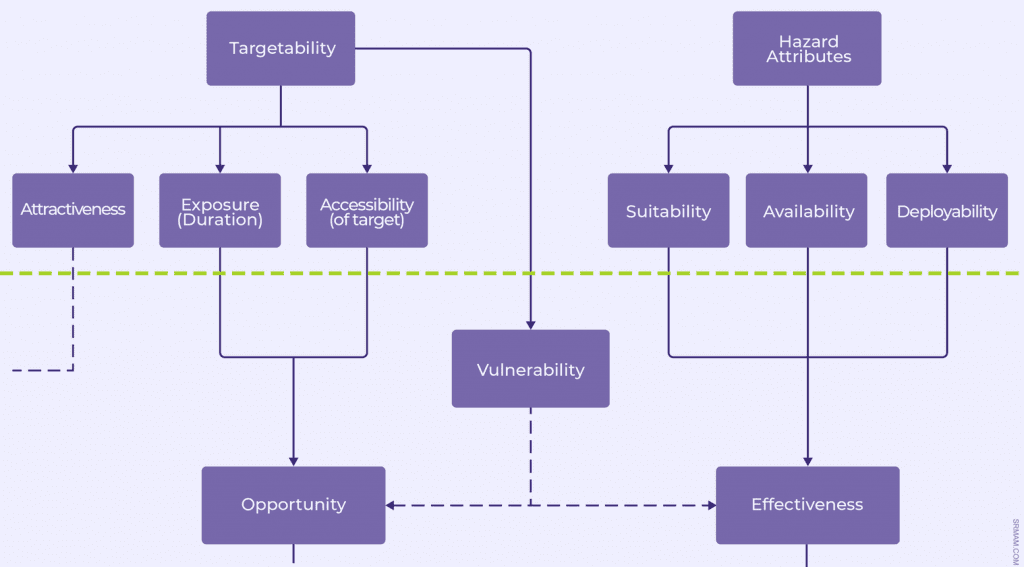
The Security Risk Assessment Context
Taking into consideration 400-odd Government Departments, Agencies and Commissions, and that there were (conservatively) upwards of 4,000 companies employing more than 200 people in early 2017 [1], plus consultants, then there is a fair base of security risk practitioners across Australian sectors. It is admittedly a conservatively educated guess, but let’s suggest that each Government entity employes at last one person that should be doing security risk assessments – two if you count those in the cyber space (because there is little difference in the methodologies applied).
Add another (again conservatively) 6,000 private sector (protective and cyber) security risk practitioners, and 500 consultants and other suppliers, and that equates to 7,300 individuals responsible for the conudct of security risk assessments (and ongoing management of associated programs). There could be triple this number, but it’s a good enough number to make the point.
In nearly 20 years of practising security risk management only a handful of security risk assessments have been observed that might be worth emulating. 99% were necessarily qualitative, but many were excessively simple, put together purely because they had to be, but otherwise offering little other than what the author wanted to do anyway.
Security Risk Methodology Rigour
There was no reasoning, no intellectual rigour and scant attention was given to integrating assets, threats and risk controls, much less vulnerability, into the narrative and calculations. Minimal justification is given to recommending spending potentially hundreds of thousands of dollars in risk ‘treatments’, and it is hard to get any kind of equivalency/benchmarks out of the results because they are so simplistic.
Then there are those in the middle and those you might describe as being overly complex; the latter are those that have usually been put together with very good intentions. Someone who goes to the effort of creating a VB scripted MS Excel Workbook, linking all of the above elements across multiple worksheets in a way that seeks to facilitate the intrinsic relationships between them all, is clearly thinking about the process.
Problems arise in the utility of the product, because most practitioners simply cannot replicate the process. Possibly, the bigger issue is when the logic is faulty though, particularly in view of the myriad of ways that the ‘art’ of security risk management can be conducted. If you have ever read HB 167:2006 in detail you’ll know what I mean.
An example of how to examine threat (supplied courtesy of SRMAM)
________________________________________________________________
RELATED ARTICLES: Musings On Security Risk Assessments | The Benefits Of SECTARA’s Advanced & Intuitive Risk Assessment Methodologies | What Is A Risk Assessment Template? | What Is A Risk Assessment Matrix?
________________________________________________________________
What the Value of a Security Risk Assessment?
The truth is that most people seem to find them an embuggerance, a stepping stone to the treatment stage. They essentially are, but they are also a critically discrete stage of the treatment process and thus warrant the highest level of attention; indeed they are meant to be the keystone in protective and cybersecurity planning.
There are many reason why such assessments are often done poorly. Emerging professional maturity levels within the industry (wihout taking anything away from the expert practitioners that are out there), a lack of rigourous oversight, low client expectations and the absence of compelling obligations to do it well. There is also confusion in the marketplace, in terms of advertised services making everyone sound like they have the best solutions/are the most expert.
Those who tend to overcomplicate the process at the expense of practicality should actually be congratulated for knowing that things should be done better and trying to do just that; it’s often easier to scale back to a good methodology than come up with one in the first place. Sometimes it works, and a few of the more advanced approaches have been what I consider best practice, but they are in the minority.
HB 167:2006 and the Security Risk Management Body of Knowledge are great places to start. If you’re a client, make sure to check the methodology, and ideally seek to examine a completed assessment before selecting a vendor. Most consultants will usually be willing to show you a redacted one in hardcopy. In doing this you will be as certain of what you’re going to get as you can be, and be in a good position to determine whether you think the logic makes sense.
How to get started with SECTARA
If you see the same great benefits that we do in SECTARA, there are several methods to get started:
- Register for one of our Bronze, Silver or Gold Plans.
- Sign up to our absolutely Free Plan.
- Arrange an online demo.
- Contact us
As a valued subscriber, you will be comprehensively supported via our Ticketing System and Knowledge Base, and you can still always contact us direct when you need to. Best of all, all subscribers are entitled to a free copy of the Security Risk Management Aide-Memoire (SRMAM) when they register (applies to both free and paid plans). SRMAM was written by Julian Talbot, the original author of SRMBoK and co-designer of SECTARA’s security risk assessment software.
We look forward to seeing you on SECTARA!
Yours in SRM,
Konrad Buczynski
Konrad was a graduate of the Royal Military College Duntroon and served as an Australian Army Officer and telecommunications specialist until 2001. He has helds roles as Director of the Australian Centre for Security Management and Chief Security Officer | Crisis/Business Continuity Program Manager at Thales Australia-New Zealand, the region’s largest Defence Prime Contractor at the time.
A Certified Practising Risk Manager, Registered Security Professional, member of numerous security working groups and technical committees and designer and author of innumerable security risk management programs, Konrad was the architect and co-founder architect of SECTARA. He is a company Principal and SECTARA’s Managing Director.