A risk assessment template is a tool that is used to document the systematic analysis of types of security risks that exist within the scope/area of an assessment, the likelihood and consequence of those risks being realised, and the recommended control measures to reduce risk to acceptable levels.
A risk assessment template can use text, graphs, charts and tables (including the risk matrix) to demonstrate risk and related attributes.
Why Use a Risk Assessment Template?
Keeping a record of all the findings in each stage of risk assessment is crucial. A sound recordkeeping system helps entities track important planning data, including the solutions selected to address current levels of risk. This can also be used retrospectively if needed to justify pre-incident planning.
A risk assessment template may be required to be used by organisations, whether it be their own or sourced from elsewhere, to be compliant with various regulatory requirements. Beyond that, it promotes communication about risk methods within organisations and workplaces.
Key SECTARA personnel have developed numerous risk assessment templates over the years. We have also seen many templates offered by others online. It caused us to question the pros and cons of using a template that is sourced online.
Clearly the temptation to a quick fix for an urgent requirement would drive many to doing this. There can be benefit in doing this, such as boilerplate content and new ideas, but there are also many potential drawbacks…
________________________________________________________________
RELATED ARTICLES: Musings On Security Risk Assessments | The Benefits Of SECTARA’s Advanced & Intuitive Risk Assessment Methodologies | What Is A Risk Assessment Template? | What Is A Risk Assessment Matrix? |
________________________________________________________________
The Pros and Cons
From a security perspective, the obvious issue includes the high potential for viruses and other malware to be embedded within free templates. If an adversary was seeking to gain sensitive information on security from organisations, what better phishing hook than content that will invariably be downloaded by security assessors. Mainstream anti-virus software doesn’t always pick up such infections either, espcially when not contantly updated.
There is also usually the issue of misalignment between your needs and the methods detailed within free risk assessment templates. It is likely to cause a practitioner much time in re formatting/structuring, with no guarantee that the result will be what’s required.
If you are a good practitioner yourself, there’s also the question of why you think someone else’s work is better than what you could prepare. For example, and because we’re based out of Sydney, Australia designed the global risk management standard (ISO 31000) and counts itself as being one of the more progressive nations in risk practices.
General Considerations and Risk Assessment Template Process
Looking past issues of online risk assessment templates, starting with a blank template can limit rapid progress and deny assessors a point of reference when completing an assessment.
The image below illustrates a basic ISO 31000 risk register, completion of which is the culmination of the risk assessment process.
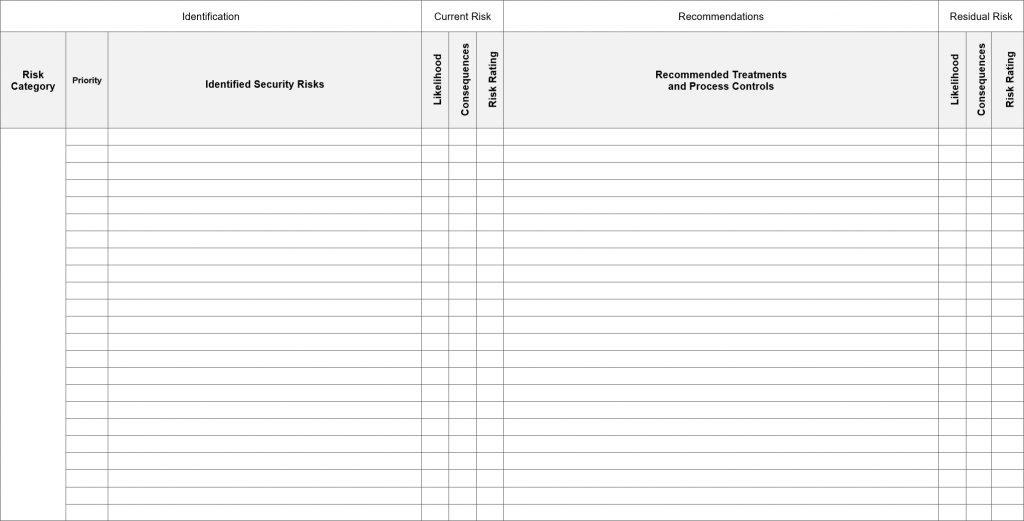
Image: Risk Register Template
However, and prior to reaching this stage in an assessment, any reasonable risk assessment template will have accounted for documenting the external, internal and security risk context. These sections of a template define the scope and various environments within which the assessment is being conducted.
They are also the appropriate places in a risk assessment template to build the business case for the assets, threats, controls, risks and recommended treatments that will invariably flow from the process.
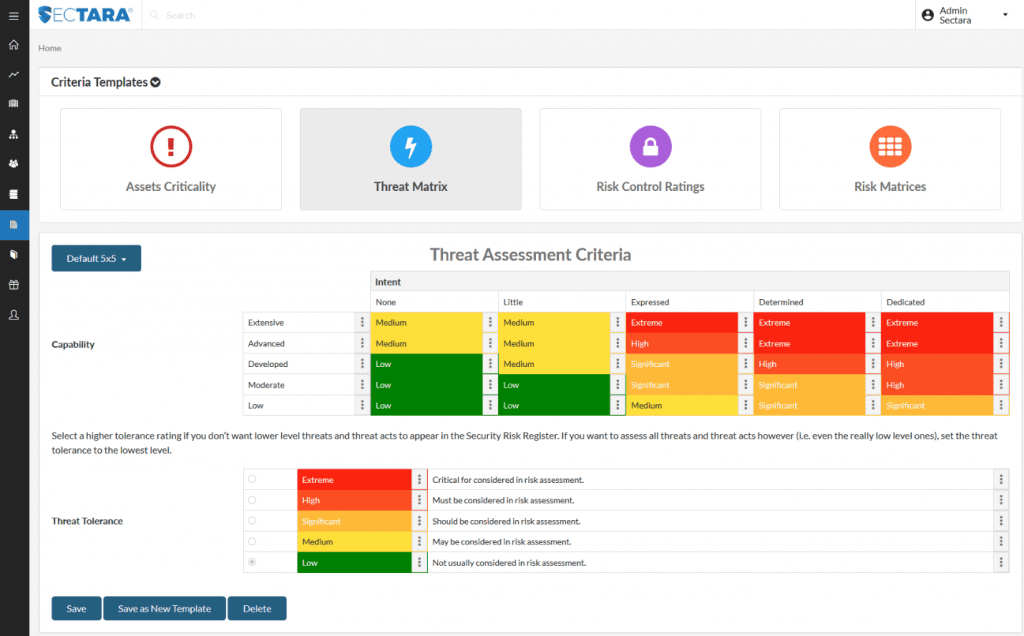
Image: SECTARA Threat Criteria Template
Subsequent stages beyond defining the context should serve to:
- identify and assess the criticality of assets;
- identify threat actors, and examine their intent and capability to carry out threat acts;
- highlight and assess the effectiveness of controls that exist to protect assets from those threat acts;
- identify areas of vulnerability;
- identify risks arising from this information; and
- recommending risk treatments that reduce the current level of risk to acceptable levels.
Using Traditional Tools
As you can imagine, it is hard to do all this effectively when using a MS Word/Excel template, for example. Much of the process of completing a risk assessment template warrants a collaborative approach to ensure the result is sufficiently informed. Working collaboratively when working remotely from each other is not easy with MS Word.
Expecting to be able to download a solution from the web, which will address your immediate needs and not leave you further confused, is unrealistic in most cases.
It was the reason for developing SECTARA. SECTARA is the official companion to the Security Risk Management Aide Memoire (SRM-AM), which is an extension of the Security Risk management Body of Knowledge (SRMBoK). It was also written by the same author (Julian Talbot), who was a SECTARA co-designer – both texts remain examplars within the industry, globally.
SECTARA addresses all the issues addressed above, including through populated libraries of data that can speed and help direct the assessment process. Relevant aspects of it also demonstrate how advanced threat assessments should be completed, and illustrates our commitment to best practice in security risk management.
Yours in SRM,
Konrad Buczynski
Konrad was a graduate of the Royal Military College Duntroon and served as an Australian Army Officer and telecommunications specialist until 2001. He has helds roles as Director of the Australian Centre for Security Management and Chief Security Officer | Crisis/Business Continuity Program Manager at Thales Australia-New Zealand, the region’s largest Defence Prime Contractor at the time.
A Certified Practising Risk Manager, Registered Security Professional, member of numerous security working groups and technical committees and designer and author of innumerable security risk management programs, Konrad was the architect and co-founder architect of SECTARA. He is a company Principal and SECTARA’s Managing Director.
Did you known that the Security Risk Management Aide Memoire (SRMAM) is free to all SECTARA subscribers (yes, even on the free plan).
How to get started with SECTARA
If you see the same great benefits that we do in SECTARA, there are several methods to get started:
- Sign up to our absolutely Free Plan.
- Register online for one of our Bronze, Silver or Gold Plans.
- Arrange an online demo.
- Contact us for Platinum Plan pricing.
As a valued subscriber, you will be comprehensively supported via our Ticketing System and Knowledge Base, and you can still always contact us direct when you need to.





