Background
There are numerous methods for identifying risks during the assessment process – and some are just plainly obvious. But if you need an assurance that everything has been done to identify them, look no further than these techniques:
- Incident Report Analysis
- Documentation Reviews.
- Brainstorming.
- Delphi Technique.
- Red Teaming.
- Intelligence Reports.
- Threat Assessments.
- Interviews.
- Root Cause Analysis.
- Swot Analysis (Strengths, Weaknesses,Opportunities And Threats).
- Checklist Analysis (eg: PESTLE, SERCL (see below), Audit Instruments).
- Assumption Analysis.
- Work Breakdown Structure.
________________________________________________________________
RELATED ARTICLES: Musings On Security Risk Assessments | The Benefits Of SECTARA’s Advanced & Intuitive Risk Assessment Methodologies | What Is A Risk Assessment Template? | What Is A Risk Assessment Matrix?
________________________________________________________________
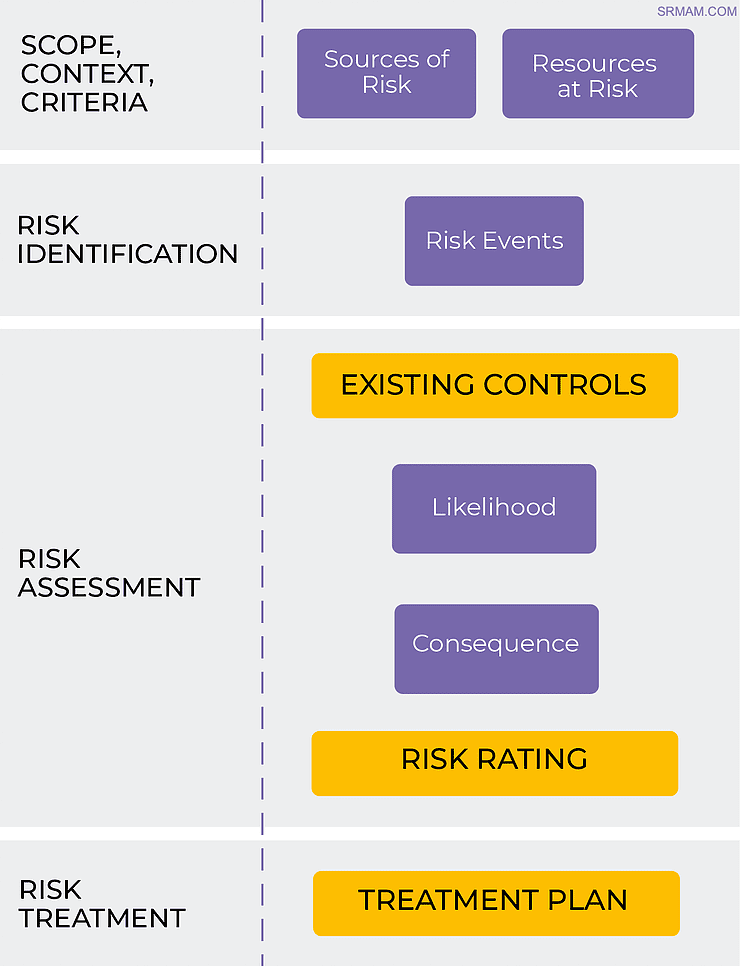
Security Events – SERCL
Security events are not the ideal way to discover and document your ‘unknown-unknowns’. Tools such as ‘SERCL’ can be a useful mnemonic for identifying risks in advance.
- Source(s): Relevant source(s) of risk?
- Event: The single key event that might be evident if this threat occurs.
- Resource(s): Resources or assets likely to be targeted or impacted.
- Consequence(s): Likely effect onResources and/or Objectives.
- Likelihood: The probability that the event will occur.It may be useful in many circumstances to consider them in the following order:
- Resources/Assets at risk
- Sources of risk
- Events which might occur
- Likelihood of attack / event
- Consequences (effect on objectives)
Not all sources of risk will involve every resource or risk event, e.g. hackers are unlikely to steal a building; but developing a list for each of S, E, & R then adding likely consequences is a good start. The following graphic highlights how the five elements of SERCL fit within theISO31000 Process.
Image: A model for risk management
Julian Talbot
Julian is a SECTARA Advisory Board Member and, among many other things, the author of the Security Risk Management Body of Knowledge (SRMBoK). In recent times Julian contemplated how to take SRMBoK further, and in doing so publish a contemporary account of associated security models, principles and practices. The result is the Security Risk Management Aide Memoire (SRMAM), a book that is free to all SECTARA subscribers (yes, even on the free plan). This article is replicated from the SRMAM wesbite with permission.
How to get started with SECTARA
If you see the same great benefits that we do in SECTARA, there are several methods to get started:
- Register for one of our Bronze, Silver or Gold Plans.
- Sign up to our absolutely Free Plan.
- Arrange an online demo.
- Contact us
As a valued subscriber, you will be comprehensively supported via our Ticketing System and Knowledge Base, and you can still always contact us direct when you need to.