Risk-related Changes to Australian Critical Infrastructure
The increasing exposure to threats faced by Australian critical infrastructure has led the Government to improve mitigation strategies to reduce risk exposures, as outlined in the recent Consultation Paper issued by the Department of Home Affairs.
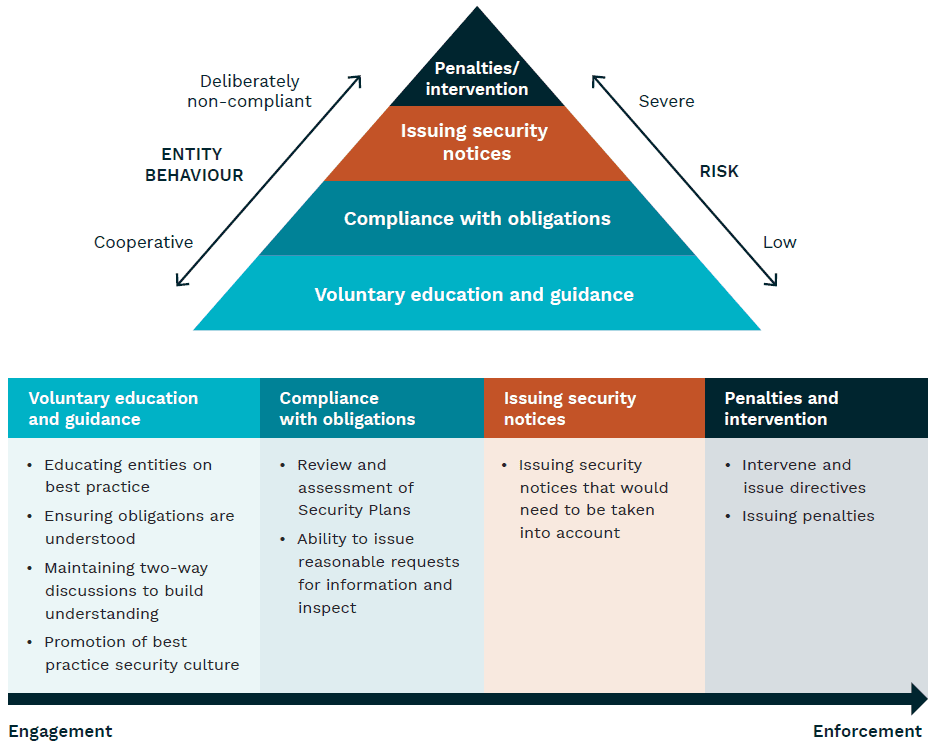
PSO Regulatory Approach Model (Source: “Protecting Critical Infrastructure and Systems of National Significance”, the Department of Home Affairs)
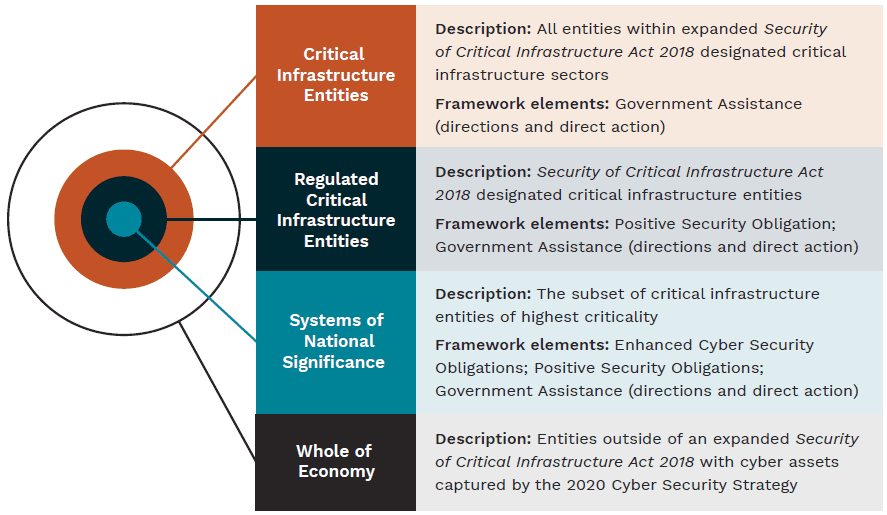
Classes of Entities and Relevant Elements of the Framework (Source: “Protecting Critical Infrastructure and Systems of National Significance”, Department of Home Affairs)
New recommended features of the enhanced framework:
Positive Security Obligations (PSO): is a combination of standard protective measures against all potential Australian Critical Infrastructure (ACI) and systems threats across all borders. PSO principles conform to ‘Regulated Critical Infrastructure Entities’ and owners and operators of ‘Systems of National Significance’ guidance, and include processes for.
- Identifying risk: Natural or human imposed actions can cause threats with significant impact on day to day critical infrastructure operations. Establishing risk-based processes to protect personal, cyber, personnel and supply chain security is crucial in identifying the likelihood and consequences of breaches and exposure to threats.
- Mitigating risk: Identifying, selecting, designing, and modifying risk mitigations to protect day to day sensitive information and other vital mission critical assets for both external and internal threat sources is crucial. Having back up measures and established recovery procedures are also mandatory to mitigate risks that may hinder the operative process of the entity, especially breaches of data confidentiality, integrity or availability (CIA).
- Governance: Entities are expected to establish ‘ISO 31000:2018 – Risk management – Guidelines’, ‘ISO 27002:2013 – Information technology – Security’, and ‘ISO 28000:2007 Specification for security management systems for the supply chain’ compliant risk assessment strategies. The purposes of this is to mitigate against highly rated risks, thus reducing potential security related breaches and loss. Such procedures require appropriate executive management oversight to ensure “accountability, demonstrated comprehensive planning and robust assurance and review processes.”
Professionals using specialised risk assessment software can conduct analysis to distinguish the distribution of identified risks and categorise them according to their variance. This supports quantitative risk assessment. Through assessing the costs and consequences of security breaches and incidents, the financial implications of proposed risk treatments can be identified.
Enhanced cyber security obligations: establishes government’s role in accessing relevant information to assess the influence and the impact of the threat on ACI prosperity and operational service delivery capabilities.
- Identifying risks: The increasing interdependence of digital transformation within critical infrastructure entities has allowed sectors of the economy to achieve efficiencies of scale in delivering goods and services across the nation. However, at the same time the data and information generated as part of the whole process has created additional exposure to cyber threats.
- Mitigating Risk: As part of the proposed 2020 Cyber Security Strategy, government involvement in obtaining relevant information is seen as crucial in creating effective mitigation strategies. In fact, in the longer term, cooperation from individual CI entities will be a legal obligation in the new amendment, where relevant information will be required on official request.
- Governance: The ‘Playbook’, which will articulate predefined responses to a range of scenarios, will also be an effective tool for the government to organise safeguards in handling threat emergencies.
- The extent of cyber threats can be infinite and exposes individual firms to outliers that may be beyond their scope, expertise and experience. Having access to essential tools to assess security controls supports implementation of appropriate risk treatments to ensure data security.As a result, the information provided by individual firms is expected to allow the government to suggest better approaches in combating different risk exposures.
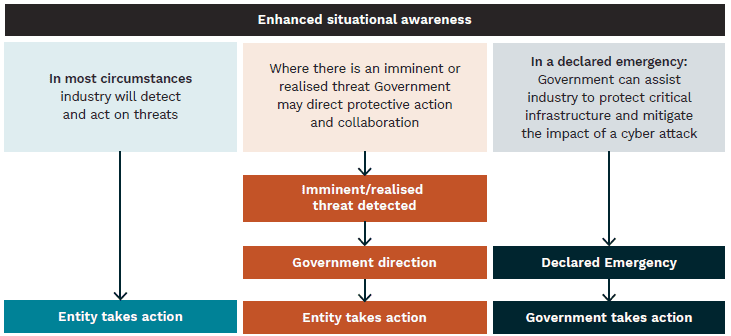 Response Model – proposed responsibilities (Source: “Protecting Critical Infrastructure and Systems of National Significance”, Department of Home Affairs)
Response Model – proposed responsibilities (Source: “Protecting Critical Infrastructure and Systems of National Significance”, Department of Home Affairs)
Cyber assistance for entities: The two-way risk mitigation approach between CI entities and the government is mandatory in identifying risks associated with individual functions and operations. In situations where the threat potentially affects national sovereignty and its Critical Infrastructure, the Government may decide upon direct action to assist in minimising the consequences of such risk.
The aim of the new amendment is to provide a legal basis for government to take direct action, if necessary, in the national interest, and mandating the cooperation of the critical infrastructure sector.
Take-aways
These moves by Government represent an unprecedented escalation and intervention into the operations of CI entities and their operations, and the fundamental tenet underpinning the initiative is effective security risk management.
Corporate security managers and consultants should all be aware that expectations are in the process of increasing markedly, leaving little room for business as usual in this space. This relates to cybersecurity, and more traditional protective security arrangements.
Areeba Khan
Areeba is a 2nd year student at the University of New South Wales, studying a Bachelor of Actuarial Studies. She was selected for an internship with SECTARA based on her excellent appreciation of quantitative risk methods.
How to get started with SECTARA
If you see the same great benefits that we do in SECTARA, there are several methods to get started:
- Sign up to our absolutely Free Plan.
- Register onlinefor one of our Bronze, Silver or Gold Plans.
- Arrange an online demo.
- Contact us for Platinum Plan pricing.
Resources:
- Department of Home Affairs (2020). Protecting Critical Infrastructure and Systems of National Significance. [online] Available at: https://www.homeaffairs.gov.au/reports-and-pubs/files/protecting-critical-infrastructure-systems-consultation-paper.pdf [Accessed 26 Aug. 2020].
- Department of Home Affairs 2019, Critical infrastructure resilience, Homeaffairs.gov.au, The Department of Home Affairs, viewed 26 August 2020, https://www.homeaffairs.gov.au/about-us/our-portfolios/national-security/security-coordination/critical-infrastructure-resilience.
- Department of Home Affairs 2019, Protecting Critical Infrastructure and Systems of National Significance, Homeaffairs.gov.au, The Department of Home Affairs, viewed 26 August 2020, https://www.homeaffairs.gov.au/reports-and-publications/submissions-and-discussion-papers/protecting-critical-infrastructure-systems.