Background
Cybersecurity has become a vital area of defence for contemporary societies, organisations and individuals. With the transition to an ‘Internet of Things’ (IoT), and a strong reliance on systems for critical infrastructure, the sophistication and intensity of associated attacks exposes us all to a significant degree of risk.
Protecting the confidentiality and integrity of information is therefore crucial. However, and since organisations are in a complex and dynamic environment, security risk measures require more robust approaches in identifying the true potential of threat exposure.
Monte Carlo Simulation
Using Monte Carlo simulation as a risk management tool can help to simulate expected risk outcomes. It can also enable decision makers to evaluate possibilities from a range of outcomes and provide probabilistic indicators of an event taking place.
Monte Carlo simulations perform a transformation of uncertain values, through chosen distribution functions by the modellers, which then produce random values. The simulation process on those random values is then calculated repeatedly, each time using a different set of random values, and storing the new output values of the model.
Upon completion of this overall process, final values can be analysed and displayed through various graphical methods. Depending upon the nature of the simulation and the chosen distribution, the results tend to take a shape of the specific distribution mapped on the range of values that were chosen initially. These can then be used to suggest statistical inferences and map probabilities of certain events.
Choosing the preferred probability distribution curve is dependent on the nature of the analysis and the demand of the modeler’s overall analysis. There are many different types of distributions that have their own unique properties that can be taken into consideration. The most common are: Triangle; PERT; binomial; Poisson; Normal; Lognormal and Uniform distributions.
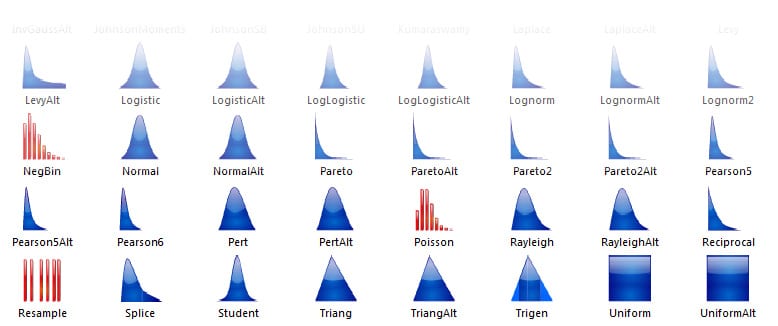
Figure 1: Distribution curves and their data mapping.
Advantages
The key advantages of using Monte Carlo simulation for Cyber security Threat include the fact that it can:
- Quantify risk likelihood for better analysis and interpretation of potential cyber threats.
- Provide an early identification of potential threat exposure.
- Be used to map out more realistic cyber threats and probability of identifying the potential asset at risk.
- Provide objective data for decision making.
- Easily allow assessors to identify the key input values that were the driving factor for the most pessimistic scenario(s).
Australia’s Cyber Security Strategy 2020
A vision for a more secure online world for Australians is contingent on the overall outlook of the country’s Cyber Security Strategy. The increasing rate of cyber threats and the continuous nature of various methods and targets by cyber-criminal threat actors has placed a huge responsibility on the Australian Government to act.
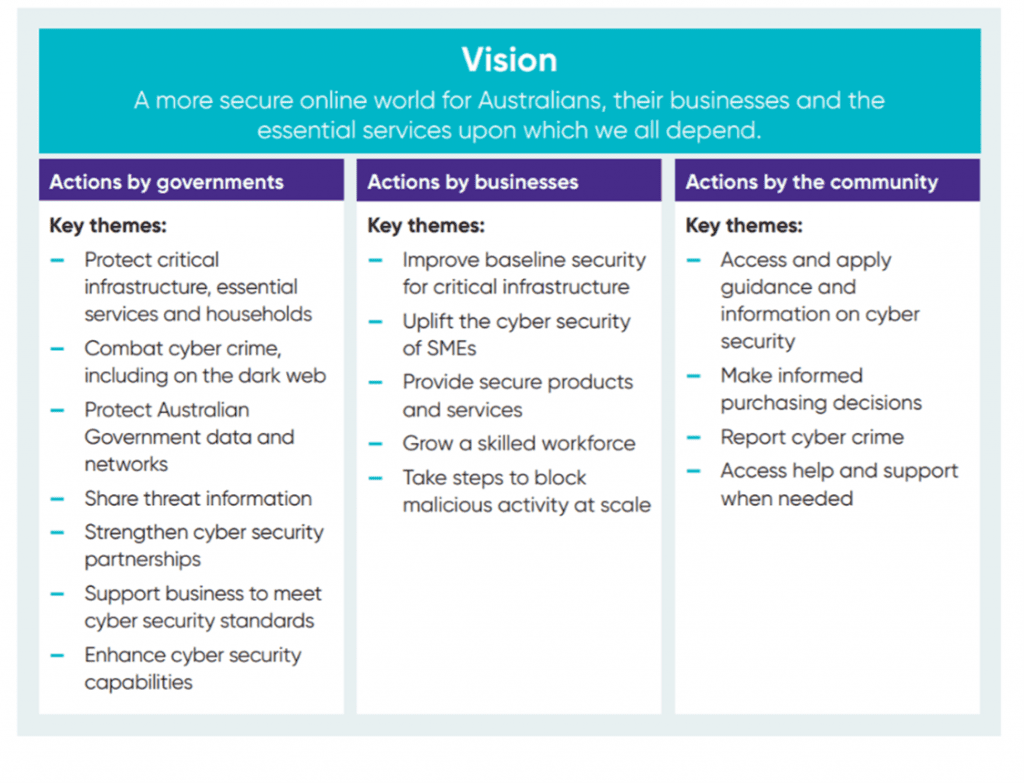
Figure 2: Illustrated Summary of Australia’s Cyber Security Strategy 2020 (Source: Australia’s Cyber Security Strategy 2020 Report)
The focus of the proposed strategy is to influence businesses and organisations to adopt methods that are effective in identifying and mitigating threat exposure. Integrating a model like Mote Carlo simulation within security risk practices can serve to enable them to predict certain events and their probabilistic impact on the assessed assets at risk.
These predicted events and situations plot risks over a wide spectrum, allowing businesses to take appropriate action to mitigate future threat exposure.
In conjunction with the 2020 strategy, ‘Supporting Organisations’ will be available to assist individual businesses to mitigate against, prepare for and respond to attacks. This will involve increased quality information, advice on contemporary methods and mapping out procedures to optimise the overall cyber-wellbeing of entities.
Using models such as Monte Carlo simulation in day to day Cyber security risk assessment processes can help to further protect everyone, businesses and governments in particular, from increasing cyber threat exposure.
Written by:
Areeba Khan
Areeba is a 2nd year student at the University of New South Wales, studying a Bachelor of Actuarial Studies. She was selected for an internship with SECTARA based on her excellent appreciation of quantitative risk methods.
How to get started with SECTARA
At the time of writing Monte Carlo simulation functionality did not exist within SECTARA, but it is coming! More broadly, if you see the same great benefits that we do in SECTARA, there are several methods to get started:
- Sign up to our absolutely Free Plan.
- Register onlinefor one of our Bronze, Silver or Gold Plans.
- Arrange an online demo.
- Contact us for Platinum Plan pricing.